Why Cloud Landing Zones Are Critical for Business Success 🎯
In today’s digital-first world, organizations are racing to the cloud. However, many discover that migrating without proper foundation leads to security vulnerabilities, compliance issues, and cost overruns that can derail entire transformation initiatives.
Cloud Landing Zones solve this challenge by providing a pre-configured, secure, and well-architected multi-account environment that serves as the foundation for all cloud deployments.
The Impact: Organizations with well-designed landing zones achieve 67% faster cloud adoption, 40% lower operational costs, and 90% fewer security incidents compared to those without proper cloud foundations.
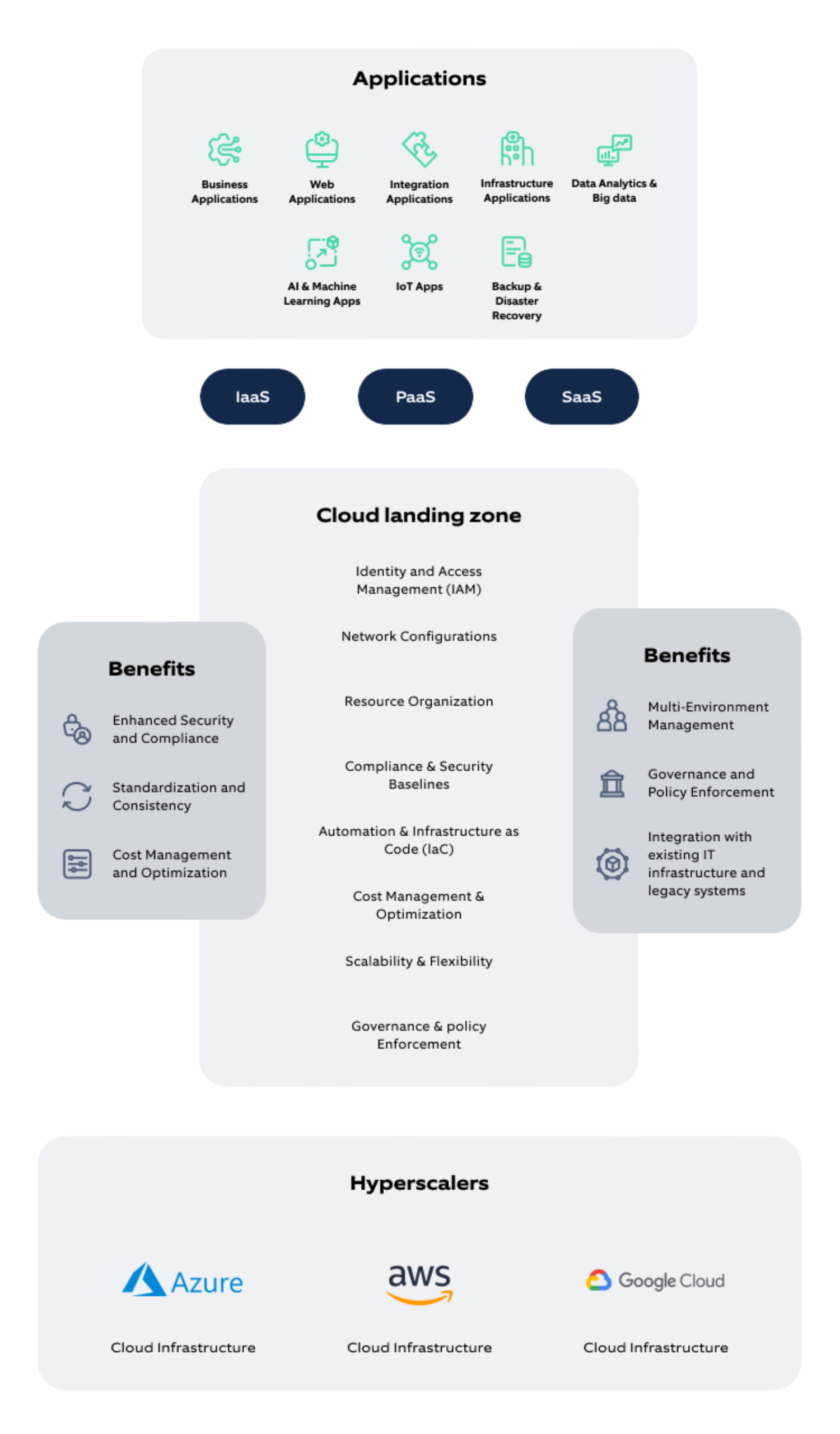
What is a Cloud Landing Zone? 🌐
A Cloud Landing Zone is a secure, scalable, and compliant cloud environment that includes:
- Multi-account architecture for workload isolation
- Centralized security and governance controls
- Standardized networking and connectivity
- Automated compliance monitoring
- Cost management and optimization tools
Think of it as the “prepared ground” where your cloud infrastructure can be built safely, efficiently, and in compliance with your organization’s requirements.
The Business Case: Why Landing Zones Are Essential 💼
1. Security and Compliance Foundation 🛡️
The Challenge: Cloud security breaches cost organizations an average of $4.45 million.
Landing Zone Solution:
- Centralized security controls across all accounts
- Automated compliance monitoring (SOC 2, PCI DSS, HIPAA, GDPR)
- Zero-trust architecture principles
- Automated incident response
Results: 90% reduction in security incidents, 75% faster compliance processes
2. Accelerated Time-to-Market ⚡
Traditional Problem: Teams spending 6-12 months setting up basic infrastructure
Landing Zone Advantage:
- Pre-configured environments ready in days
- Standardized templates for common patterns
- Self-service capabilities for development teams
- Built-in operational excellence
Impact: 67% faster application deployment, 50% reduction in setup time
3. Cost Optimization 💰
Common Issue: 32% of cloud spend is wasted on average
Landing Zone Controls:
- Account-based cost allocation and tracking
- Automated cost monitoring and alerts
- Resource optimization policies
- Reserved instance management
Savings: 30-40% reduction in overall cloud costs
Core Components of a Landing Zone 🧩
1. Multi-Account Structure 🏢
Core Accounts:
- Management Account: Central billing and organizational control
- Security Account: Centralized security tooling
- Shared Services: Common infrastructure components
- Log Archive: Centralized audit trails
Workload Accounts:
- Production, non-production, and sandbox environments
- Organized by business unit, application, or environment type
2. Network Architecture 🌐
Hub-and-Spoke Design:
- Central transit gateway for routing
- Isolated VPCs for different workloads
- Secure connectivity to on-premises systems
- Network monitoring and traffic inspection
3. Security Framework 🔒
Identity and Access Management:
- Single sign-on (SSO) integration
- Role-based access control
- Multi-factor authentication
- Just-in-time access provisioning
Security Controls:
- Service control policies for account boundaries
- Automated compliance monitoring
- Threat detection and response
- Data encryption and protection
4. Operational Excellence 📊
Monitoring and Observability:
- Centralized logging and metrics
- Automated alerting and notifications
- Performance monitoring dashboards
- Cost tracking and optimization
Cloud Provider Solutions 🌩️
AWS Control Tower 🚀
- Automated account provisioning with baseline configurations
- Guardrails for governance and compliance
- Centralized dashboard for organizational oversight
- Built-in best practices and security controls
Azure Landing Zones 🔷
- Enterprise-scale architecture patterns
- Management group hierarchy and subscription design
- Azure AD integration and RBAC implementation
- Hub-and-spoke network topology
Google Cloud Foundation Toolkit 🌈
- Project factory for automated provisioning
- Organization policies for governance
- VPC service controls for network security
- Security Command Center integration
Industry-Specific Requirements 🏭
Financial Services 🏦
- SOX, PCI DSS, and Basel III compliance
- Enhanced data encryption and audit trails
- Strict network segmentation
- Regulatory reporting automation
Healthcare 🏥
- HIPAA compliance for protected health information
- High availability for critical systems
- Integration with existing healthcare systems
- Comprehensive access logging
Government 🏛️
- NIST Cybersecurity Framework compliance
- FedRAMP and FISMA requirements
- Data sovereignty and access controls
- Detailed audit and incident reporting
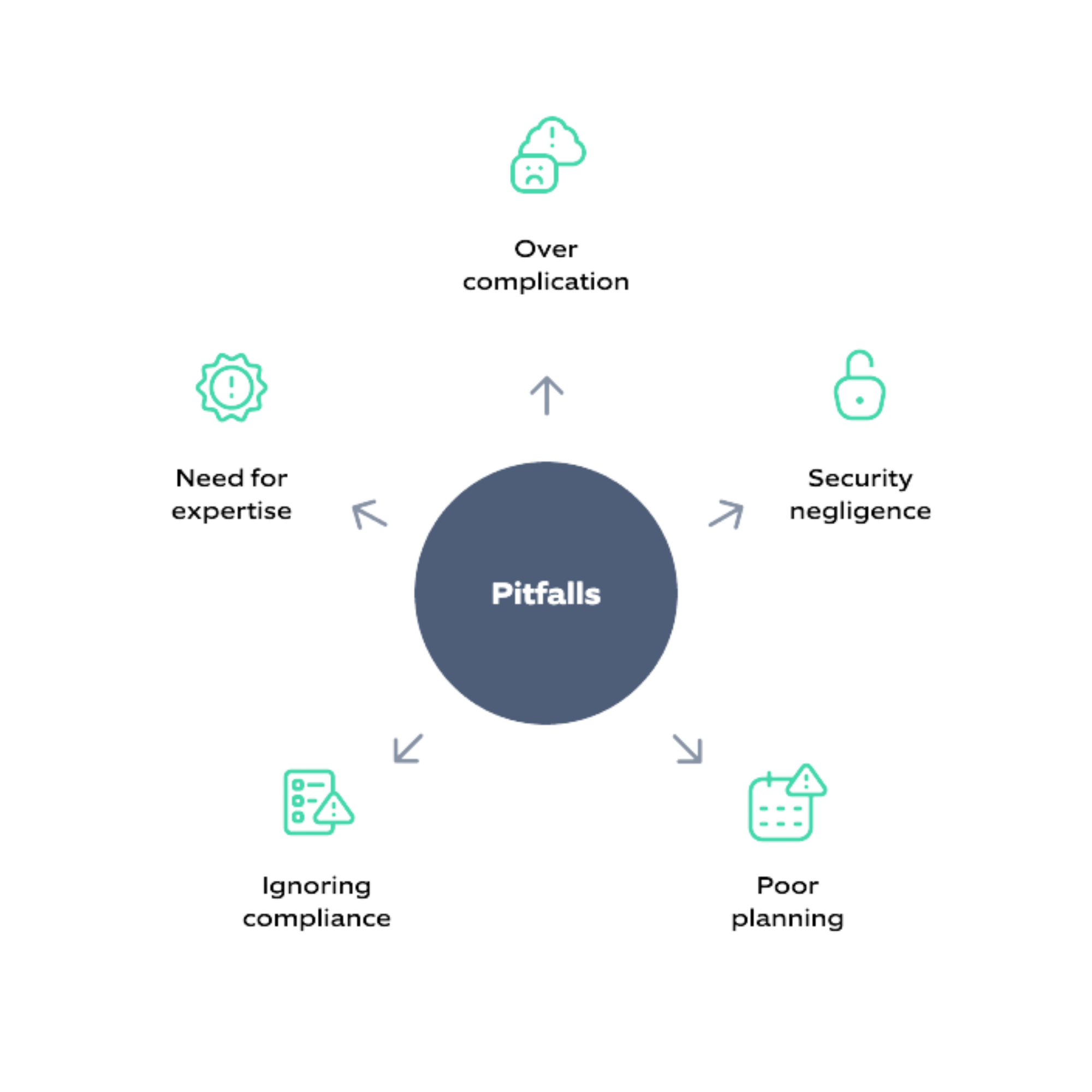
Common Pitfalls implementing Landing Zone:
The Future of Landing Zones 🔮
Emerging Trends
- AI-powered optimization for automated resource management
- Edge-to-cloud integration for distributed architectures
- Sustainability focus with carbon footprint tracking
- Zero-trust security with comprehensive identity verification
Why Choose Professional Landing Zone Services? 🤝
Expert Implementation
Ongoing Support
Business Benefits
- Reduced implementation risk
- Faster time to value
- Lower total cost of ownership
- Enhanced security and compliance posture
Your Cloud Success Starts Here 🌟
Cloud landing zones are not optional—they’re the critical foundation that determines whether your cloud transformation succeeds or struggles. Organizations with well-architected landing zones consistently outperform their peers in security, cost efficiency, and operational excellence.
The choice is clear: invest in a proper cloud foundation now, or face the consequences of cloud chaos later.
Don’t let inadequate infrastructure limit your cloud potential. Build the right foundation from day one.
Ready to Transform Your Cloud Journey? 🚀
Get Started Today:
🔍 Free Cloud Assessment: Evaluate your current cloud readiness 📊 Strategy Workshop: Design your optimal landing zone architecture
🏗️ Rapid Implementation: Deploy your landing zone in weeks, not months 🛠️ Managed Services: Ongoing optimization and support
Contact our cloud experts today and build the secure, scalable foundation your business deserves.
Transform your cloud transformation with a world-class landing zone. Our certified architects have successfully implemented solutions for Fortune 500 companies across every major industry.


